2015 in breaches: The year digital attacks got personal
Loading...
The good news? Data thieves made off with less of America’s financial data in 2015.
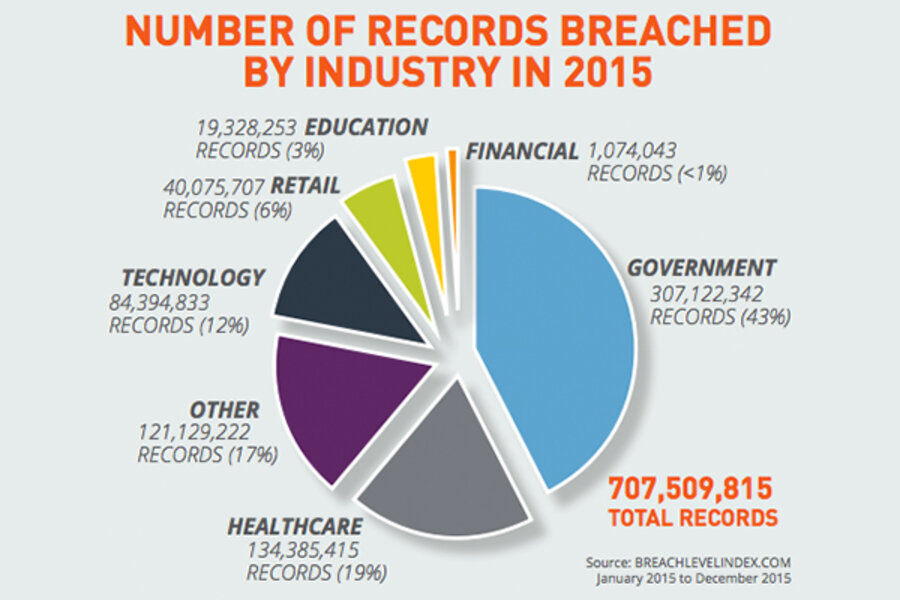
The not-so-good news? Digital attackers plundered far greater – and more valuable – amounts of personal information from government and healthcare databases.
What changed isn’t the number of break-ins so much as what hackers were able to haul away during a breach, according to the 2015 Breach Level Index compiled by digital security firm Gemalto.
The trend lends new urgency to encryption and other strategies to safeguard data.
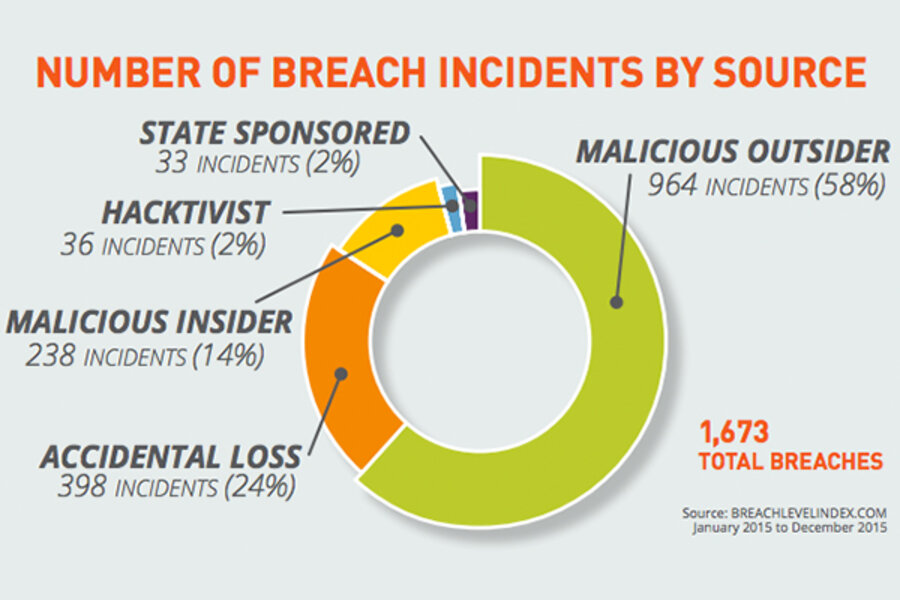
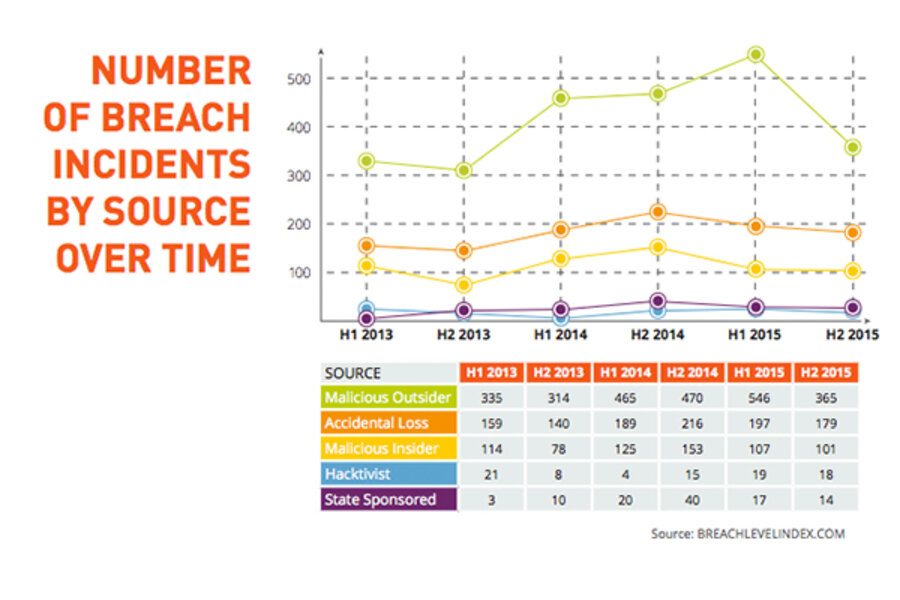
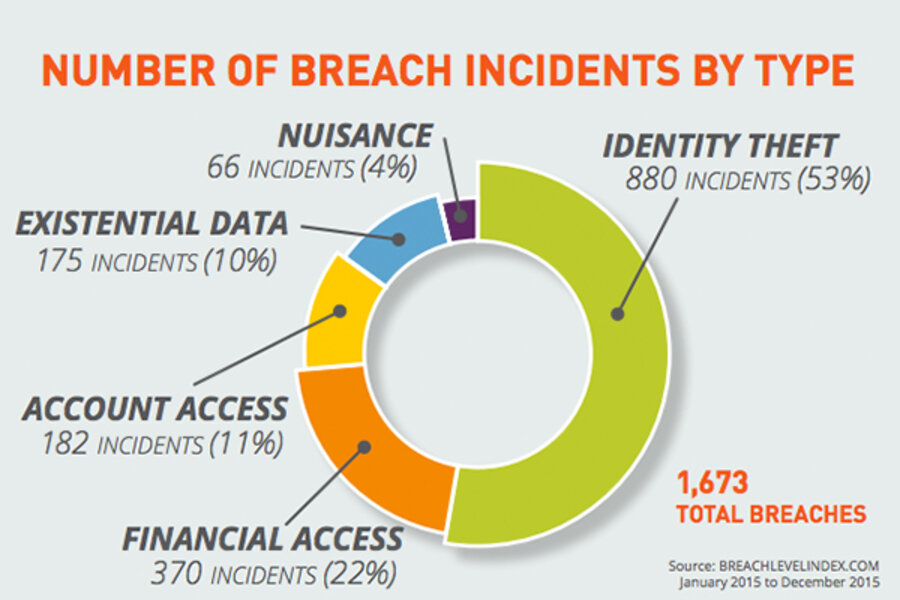
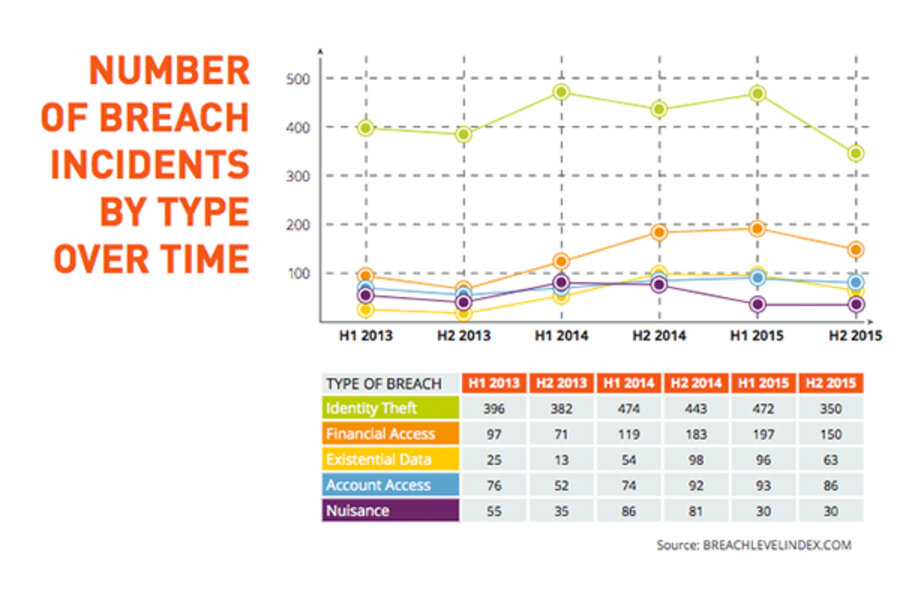
The Breach Level Index aggregates publicly-available information on data breaches worldwide and analyzes trends in sources, targets, and severity. Since Gemalto first began compiling this data in 2013, more than 3.6 billion data records have been exposed.
Hardened by years of high-profile attacks, retail saw a 93 percent drop in the number of records stolen in 2015 compared with 2014 despite a slight uptick in breaches. The story was similar with financial companies. Meanwhile, the number of government records stolen surged 476 percent, joined by a 221 percent spike for healthcare industry records.
None of these industries can point to clear success preventing breaches, calling into question security strategies that focus purely on keeping hackers out. Instead, the experience of retail and finance show that big progress can happen in limiting the severity of theft, even without bringing down the number of breaches.
“It is important to keep in mind that not all breaches are equal in terms of the level of severity and damage that they can bring for companies and their customers,” said Jason Hart, vice president and chief technology officer for data protection at Gemalto. “Even if a breach occurs, it can be a secure breach if the right security technologies, such as encryption, are properly in place to protect the most important and sensitive data.”
Encryption is the first of three recommendations from Mr. Hart to lessen the impact of a breach. Next is safeguarding the encryption keys, followed by multi-factor authentication.
Limiting the losses
Less expansive thefts have reduced the pressure on the retail sector following a bruising 2014, when it faced the loss of more than 567 million data records. Last year, that figure dwindled to 40.1 million, a reduction that means dramatically less litigation, reputational damage, and cleanup costs.
The industry had little choice but to focus on digital security given intense scrutiny by both the media and lawyers. The retail sector has borne the brunt of class action lawsuits for data theft, facing 80 percent of such suits, according to a 2015 report in the Journal of Consumer & Commercial Law.
The average cost to a company per stolen record in 2015 reached $154, according to a 2015 report from the Ponemon Institute, meaning this year’s drop in theft saved the retail industry somewhere in the ballpark of $80 billion in 2015.
Despite the encouraging signs in the retail and finance sectors, it’s not clear how much these reflect changed security strategy versus changing demand on the black market.
Few victims used encryption
One area that could stand clear improvement: While encryption is one of the most obvious strategies for preparing for a breach, only 48 of the data breaches in 2015 – less than 4 percent of all breaches – involved data that was encrypted to any degree. Implementing extensive data encryption has a proven impact on bringing down the cost of a breach: The Ponemon study found it shaved $12 off the per stolen record cost borne by breached companies.
Encryption is a particularly crucial tool in safeguarding the kinds of sensitive information that hackers are taking from medical and government databases. Credit card numbers nabbed from a retailer can be cancelled and replaced in a matter of minutes; social security numbers less so. Medical records are being used by hackers to procure expensive operations in a crime that often doesn’t come to light until months later.
“In 2014, consumers may have been concerned about having their credit card numbers stolen, but there are built-in protections to limit the financial risks,” said Hart with Gemalto.
Attacks on personal information and identities, however, are much harder to remediate, meaning companies with lax security risk a much stronger backlash. “If consumers entire personal data is being coopted so thieves can rob their houses, compromise their cars, or steal their identities again and again, the calculus will change and so will consumer trust in the companies they do business with,” he said.
Read the full report with the latest data from Gemalto’s Breach Level Index, a global database of data breaches that calculates their severity on multiple dimensions.