Terrorists’ best weapons: guns, bombs, Twitter
Loading...
Twitter users following the deadly Westgate mall attack in Nairobi, Kenya, late Monday would have breathed a sigh of relief when the Kenyan Interior Ministry (@InteriorKE) tweeted their forces were in control of the situation after four days of fighting and 62 people killed.
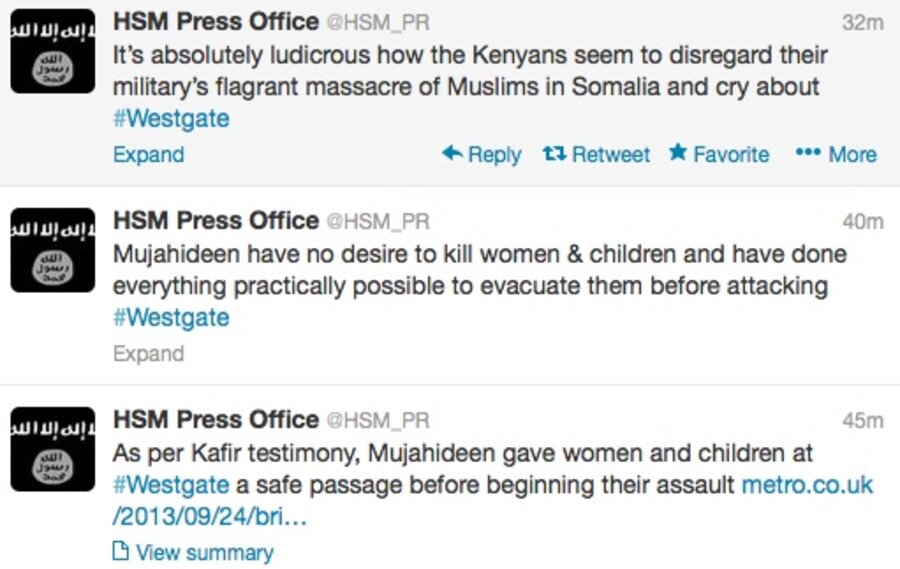
But on elsewhere on Twitter, a different message appeared. The terrorist group behind the attack – Somalia-based, al-Qaeda-affiliated al-Shabaab – tweeted an ominous message the next morning from @HSM_PR:
"#Westgate attack is now into its fourth day but the operation is far, far greater than how the Kenyans perceive it in their minds."
Though al-Shabaab is the most recent group to broadcast their message online, terrorist groups have been using social media for publicity and recruitment for many years. It's been a tool that has advanced their message into the Western world and brought further attention to their acts of terror.
Al-Shabaab (which means “The Youth” in Arabic) first joined Twitter in 2011 as @HSMPress, linking to audio files of the sounds of captured soldiers and sharing suicide-bomb body counts. They were active on the site, responding to tweets and amassing thousands of followers. Fast forward to last weekend: their tweets focused on updates about the “success" of the attack in Nairobi. Twitter suspended five of their accounts throughout the weekend, but al-Shabaab continued to open new accounts. And each new account garnered thousands of followers in a matter of hours, an impressive feat, had the circumstances been better.
“Terrorists never invented anything about the Internet; they didn’t design anything online, but they learned very fast how to learn the latest innovations in cyber space,” says Gabriel Weimann, a fellow at the Woodrow Wilson International Center for Scholars in Washington and author of the upcoming book “Terrorism in Cyberspace: The Next Generation.”
Mr. Weimann has been tracking terrorists’ use of online media for more than 15 years. When he started in 1998, his team was only looking at 12 sites, which he says were very primitive. Now they monitor more than 9,600 sites that range from chat rooms and Web forums to social media sites such as Twitter, Facebook, and even Google Earth. “If you were a terrorist, how would you enjoy having free satellite [image] services at your disposal?” he says.
He says the enormous increase in the online presence of terrorism groups is due to “narrowcasting” instead of broadcasting. Terrorism groups split up their online activities to focus on different target audiences, such as overseas populations, women, and even children. The aim is not unlike any other marketing strategy: by fine-tuning their message, they can recruit specific groups.
And al-Shabaab is hardly the only group to use social media. The Taliban has a Twitter account (@alemarahweb), same with Hezbollah (@almanarnews) and Hamas (@AlqassamBrigade), along with many other smaller organizations. Facebook has also been used to create both official and unofficial pages for terrorist groups, though a study from the Middle East Media Research Institute (MEMRI) in Washington found that Facebook is active in suspending accounts linked to terrorism.
The flow of terrorists online also poses problems for social media sites that are based on principles of free speech and offer a platform for connecting people. Twitter, for example, didn’t take down al-Shabaab’s initial account until January 2012, when the group posted a gruesome photo of a dead French soldier killed in a hostage rescue attempt. This blatantly violated Twitter’s Terms and Conditions, which says “You may not publish or post direct, specific threats of violence against others” as well as “You may not use our service for any unlawful purposes or in furtherance of illegal activities.” A month later, al-Shabaab rejoined the site with a different handle.
On the other hand, Twitter has not taken down the Taliban’s account, arguing that the group is not registered as a Foreign Terrorist Organization.
Twitter did not respond to a request for comment regarding terrorists using its site.
Though their radical tweets may be unsettling, terrorists’ ongoing social media presence has allowed extensive monitoring by academic groups, the government, and local activists. Weinmann’s group archives every terrorist-issued tweet, message, or YouTube clip they find. MEMRI recently released a three-part study called "Jihadi Media Foundations on Facebook and Twitter." The International Security Assistance Force flags suspicious Taliban tweets. Minneapolis-based anti-terrorism activist Abdirizak Bihi, profiled in this Washington Post article, makes it a regular part of his day to search Facebook and chat rooms to monitor al-Shabaab recruitment.
Initial reports say one or two of the terrorists involved in the Nairobi attack are allegedly from the United States. If this proves to be true, online media may have helped bring al-Shabaab’s message across the world from Somalia to the US.
But it also may help people understand how a person can evolve from civilian to terrorist. Weimann says some of the most difficult attacks to understand and predict are the "lone wolf" attacks, like the Boston Marathon bombings, or even young men recruited to join overseas groups. Tracking the online and social media interactions of terrorist groups, however, often shows that the terrorist did not radicalize and train themselves. That comes from a much larger group, contacted through the cyber world.
"You saw only the attacking wolf, but there is a virtual pack behind them," he says.