Energy sector cyberattacks jumped in 2012. Were utilities prepared?
Loading...
Cyberattackers zeroed in on computer systems run by power grid operators and natural gas pipeline companies last year, paying less attention to infiltrating networks belonging to water, chemical, and nuclear facilities, a new federal report shows.
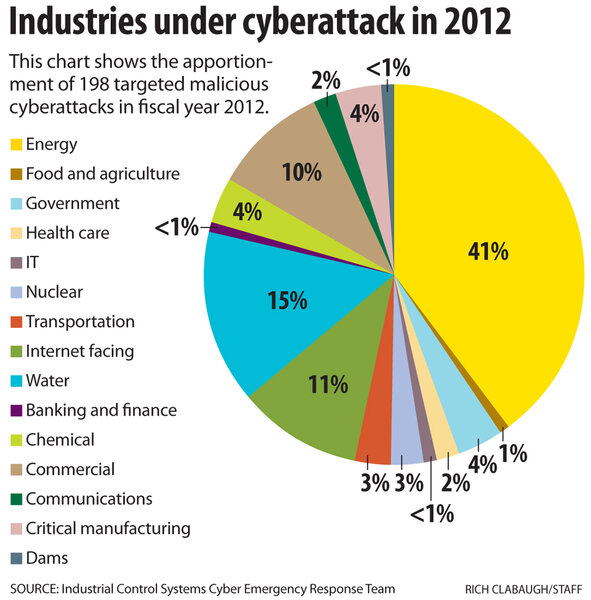
Energy companies were clearly in the cyber bullseye in 2012, targeted in 41 percent of the malicious software attack cases reported to a special Department of Homeland Security (DHS) team that responds to cyberattacks on industrial computer networks.
The overall number of attacks remained flat at 198 incidents for the year, the same as 2011. But energy sector companies reported 82 cyberattacks last year, a sharp increase over the 31 cases reported in 2011, according to a report released last week by DHS's Industrial Control System-Cyber Emergency Response Team (ICS-CERT).
Among those energy-sector cyberattack cases, 23 involved oil and natural gas companies hit by a persistent months-long targeted spear-phishing campaign first reported by the Monitor in May. Also on the upswing were attacks on commercial manufacturing facilities that leaped to 19 last year from 2 in 2011.
Water systems were close behind among sectors most targeted, but still saw far fewer attacks compared with 2011. Cyberattacks reported on water plants fell to 19 incidents or 15 percent of last year's total compared with 81 attacks and a 41 percent share of the total when it was the largest single targeted sector in 2011.
Reported attacks on chemical companies also fell from nine to seven. Nuclear power and other facilities, which were in their own category separate from "energy," saw six reported incidents last year compared with 10 in 2011, the ICS-CERT report found.
What the numbers indicate is cyberspies focusing their efforts increasingly on the energy industry and less on everything else, experts say.
"Campaigns are widening to include a successful attack against a key supplier of energy control systems and attempts to compromise a sector security consortium," writes Michael Assante, former chief security officer at the North American Electric Reliability Council, whose member companies run the nations' power grid, in an online comment on the DHS report. "Energy will continue to be an attractive target."
Despite increasing awareness of the threat, companies that rely on computerized systems for production – especially those in the energy sector – have a long way to go to defend themselves against sophisticated cyberspies, who are practically unimpeded in their efforts to map networks, set up digital beachheads inside networks, and steal e-mail, data and passwords, experts in industrial control system security say.
"Unfortunately, most utilities just aren't prepared from a resources perspective for the coming threats," says Robert Huber, a principal at Critical Intelligence, a cybersecurity firm in Idaho Falls, Idaho, that specializes in protecting critical infrastructure. "They have neither the necessary people, nor the budget."
Debate has been rising over how best to protect "critical infrastructure" companies, including those that operate the power grid, gas pipelines, transportation, water, chemical, financial, and other networks. But awareness of the depth of the problem is giving at least some company officials a fresh perspective on the risks involved.
Over the past decade many companies have linked their Internet-connected business networks to the industrial control networks. While these connections allow company managers to tap real-time production data and lower costs, they also have created a point of entry for cyberattackers intent on gaining access to the control systems.
President Obama has promised to soon deliver a new executive order increasing federal agency oversight of cybersecurity involving industrial sectors if Congress does not act.
One example: In response to a distress call, ICS-CERT sent a rapid-response team to provide onsite support at a power generating plant "where both common and sophisticated malware had been discovered in the industrial control system environment."
The malware had been discovered when an employee, who routinely used a USB drive to back up control system configurations, asked the company IT staff to inspect his USB drive after experiencing problems with the drive’s operation. A scan with up-to-date antivirus software revealed three positive hits, including one sample "linked to known sophisticated malware." (Such infections spread by USB drive are believed to be the way that the cyberweapon Stuxnet infected Iran's nuclear fuel complex.)
After that, the ICS-CERT team found the same sophisticated malware on the two engineering workstations. A check of 11 other workstations showed them to be clear. But the two with the infection were so vital that, at the time, they could not be shut down to have the malware removed.
"The organization also identified during the course of the investigation that it had no backups for the two engineering workstations," the ICS-CERT report last week said. "Those workstations were vital to the facility operation and, if lost, damaged, or inoperable, could have a significant operational impact."