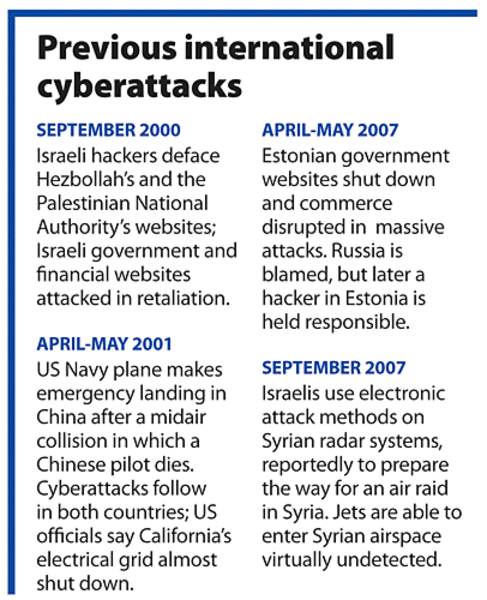
Cyberspace: new frontier in conflicts
Loading...
| Oakland, Calif.
As Georgian troops retreated to defend their capital from Russian attack, the websites of their government, also under fire, retreated to Google.
In an Internet first, Georgia's Ministry of Foreign Affairs reopened its site on Google's free Blogger network and gave reporters a Gmail address to reach the National Security Council.
The attacks have deluged the websites of the president, various ministries, and news agencies with bogus traffic. The jam not only shut down those sites but also clogged Georgia's Internet access, exposing its reliance on Russian Internet pipelines.
Some in the cybersecurity community say this may be nothing more than grass-roots "hactivism," which usually springs up during international confrontations. Others, however, warn that the attack highlights the leverage some countries have gained over adversaries by laying down fiber-optic cables and providing cheap Internet services.
"The lesson here for Washington is that any modern conflict will include a cyberwarfare component, simply because it's too inexpensive to be passed up," says Bill Woodcock, research director at Packet Clearing House, a nonprofit Internet research institute in San Francisco. "The best [defensive] strategy is always preparedness. We've spent eight years completely ignoring that, while the Chinese and Indian governments have been paying really close attention and investing many tens of billions of dollars."
Georgia's Internet infrastructure has two big weaknesses. First, most of its external connections go through Russia. Second, there's a lack of internal connections called Internet exchange points. So when a Web surfer in Georgia calls up a Georgian Web page, that request routes through another country, which is similar to driving to Mexico to get across town in San Francisco, says Mr. Woodcock, whose organization helps countries build their own Internet exchange points.
"If you look at how the routing is done on the Internet, there are a few major networks that are providing interconnectivity to everyone else," says Dmitri Alperovitch, director of intelligence analysis at Secure Computing Corporation, a data-security firm based in San Jose, Calif.
A problem for 110 nations
By one count, 110 nations are saddled with the problem. Former Soviet states in particular are poorly connected and increasingly reliant on Russia, he says. That's in part due to the legacy of the Soviet period. But now it has more to do with Russia's ability to offer superior Internet service through its investments in infrastructure. The situation is somewhat analogous to the more-widely-noticed reliance that neighbors have on Russia's energy pipelines.
China and India have been laying even more fiber-optic cable than Russia, allowing them to offer cheap prices and snatch away much of the Asian Web traffic that at one time flowed through Palo Alto and Los Angeles, says Woodcock.
Shoring up the cyberdefenses of friendly governments could involve laying new fiber to be price-competitive with adversaries, establishing Internet exchange points, and building up expert strike teams that can respond rapidly to attacks, cybersecurity experts say.
The Baltic nation of Estonia, which last year weathered significant cyberattacks, has dispatched two computer experts to help Georgia, according to Katrin Pärgmäe, an Estonian spokeswoman.
The attacks seen on Georgia were shorter, but more intense, than those seen in Estonia, says Jose Nazario with Arbor Networks, a network-security firm in Lexington, Mass. They have also gone in both directions at times, with some limited attacks on Russian sites. Despite Russia's military halt, cyberattacks were still reported against some Georgian sites as of press time Tuesday. "I don't see a cybertruce, but I'm not seeing devastating effects as well," he says.
Cyberattack began July 20
Georgia was under cyberassault as early as July 20, when the president's website was barraged with traffic, according to André DiMino with Shadowserver, an Internet-based security watchdog group.
The computer used to lead that initial assault, known as a denial of service (DOS) attack, was in the US and was shut down fairly quickly, he says. Then DOS attacks resurged over the weekend, this time with a leading machine in Turkey.
The locations of the machines mean little, however, since nefarious hackers and crime syndicates are able to hijack computers across borders.
Experts like Mr. DiMino and Gadi Evron, a former Israeli computer-security official, say they've seen no indication yet that the attacks are more sophisticated than something that could be done by hactivists.
"It's obvious they are suffering from serious attacks, but saying this is an Internet war is blowing it out of any possible proportion before we have more information," says Mr. Evron.
Others, including Mr. Alperovitch and Woodcock, see the DOS attacks as more sophisticated in the way they have choked the limited data pipelines that Georgia depends on.
Indeed, much of Georgia's remaining connectivity has come through non-Russian pipes, Woodcock says.
Sources and methods aside, there's broad agreement that cyberattacks can be so cheap and distracting as to be a no-brainer once bullets start flying.
Alperovitch describes such attacks as "psy-ops," comparable to bombing radio towers to stifle an opponent's ability to get its message out.
Georgia's online retreat to Google was also no doubt demoralizing.
In a long-term conflict, says Woodcock, such an attack could serve longer-term goals.
"You can bet that these attacks have cost Georgia's private sector far more than the perhaps $2,000 it cost the [perpetrators] to do them," he says.
"And in the long run, that loss of national productivity affects not only Georgia's financial ability to wage war, but its people's willingness to engage in it," he adds.